In the cybersecurity world, one of the biggest challenges is technology adoption. The degree of adoption is directly proportional to the level of ease of use and required amount of business functionality. This is why some of the highly secure products have failed because either they lack the functionality or they are too clunky to use.
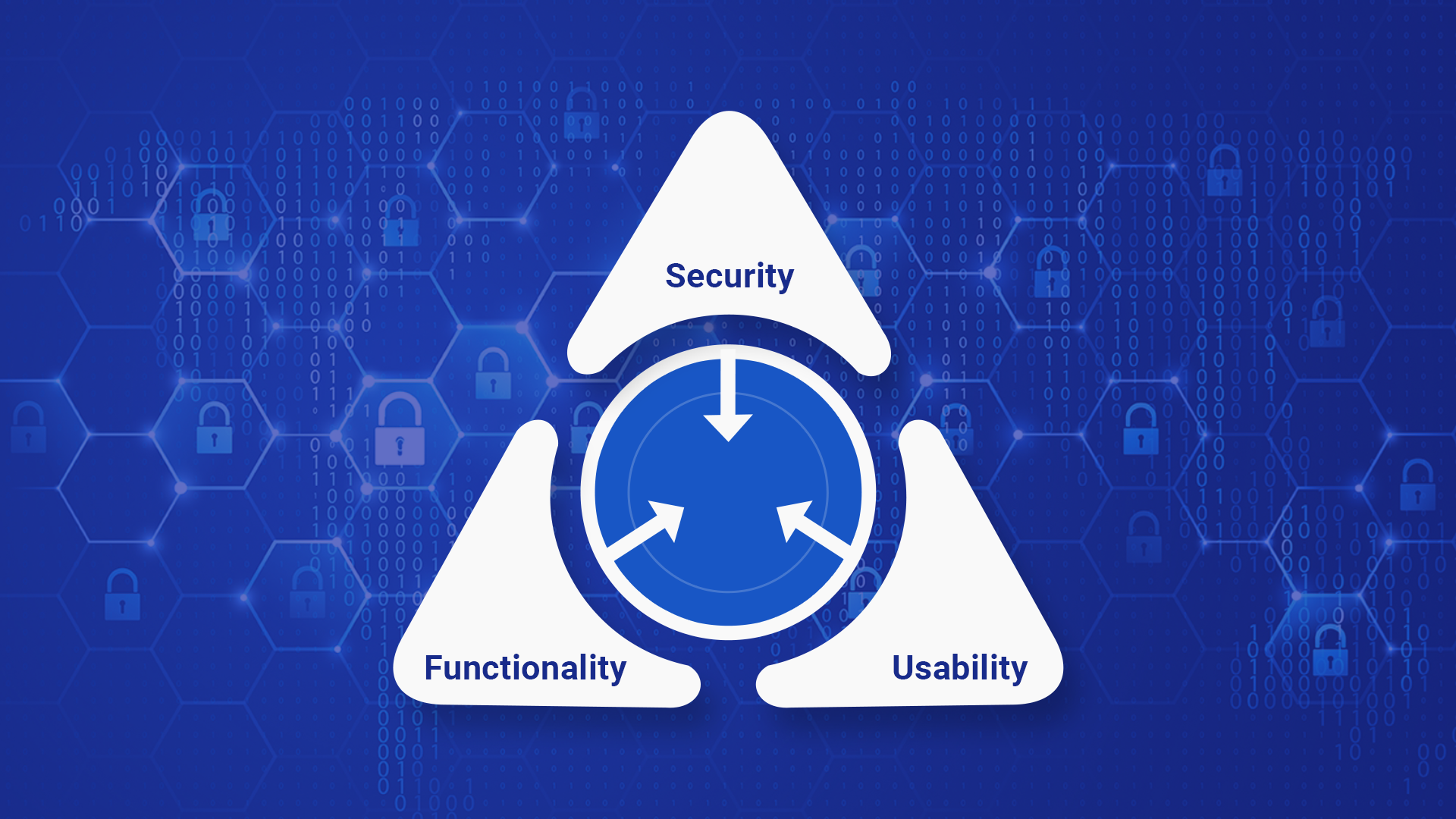
We, at DropSecure, believe that to create a useful SaaS product, the product team needs to strike the right balance among three main elements – Security, Functionality and Usability. In most cases, there is a trade-off among these three elements.
In the last decade, often the product is developed to provide a set of functionalities then the functionalities are optimised to achieve ease of use and then a security layer is applied like sprinkles on cake!
Now the product is created, let’s secure it!’ This old-school approach has been disastrous for many players in the file share and cloud storage industry.
Some of the big players from last decades are struggling to offer adequate security on their product offerings mainly because security has always been an afterthought in their product design approach. They are finding it extremely difficult now to secure the whole bouquet of features (arguably many of them are completely unnecessary). No wonder why their security gets breached so often.
In fact, many of them are now forced to partner with other security solutions but many security experts believe that it’s more of a patch work and such combinations fail to provide a comprehensive security protection. In contrast, DropSecure was conceived with these three elements right in the centre of the development process. Therefore, in our case, security is not an afterthought – it is the product!
It’s important to understand the holy triad of product development.
A triangle can be used to help explain the relationship between the concepts of security, functionality and usability – because there is an inter dependency between the three attributes. An increase or decrease in any one of the factors will have an impact on the other two.
Functionality
It can be defined as one or all of the operations that a software program is able to perform. It’s a known fact that increasing the number of functionalities in an application will also increase the surface area that a hacker can attack when trying to find an exploitable weakness. Therefore, when an application has too many functionalities, the level of security should always be questioned.
Usability
It can be defined as the degree to which something is able or fit to be used. The trade-off between security and usability is a common challenge in the real world, and often causes friction between users and those responsible for maintaining security. Especially, when security is an afterthought. Clunky products are often the outcome of such trade-offs.
Security
It can be defined as all the measures that are taken to protect a system, application or a device as well as ensuring that only people with permission to access them are able to.
A study of users from IT-companies and banks found that while users state to be motivated and knowledgeable about security, many did not perform individual action. They considered security measures to be impediments to work. Also, requirements of expected security behaviour and awareness campaigns had little effect on user behaviour.
But weakening security to improve functionality and usability will lead any systems to be vulnerable to attack so there needs to be a way to maintain ease of usability and functionality without compromising security.
The DropSecure Approach
From the conception, we knew that to be truly effective, security needs to be built-in from the ground up. Therefore, DropSecure is built with Secure by Default philosophy. Secure by Default is about taking a holistic approach to solving security problems at root cause rather than treating the symptoms. DropSecure is powered by Zero Knowledge Encryption – this technology makes every single interaction secure by default. You can read more about The Power of Zero Knowledge Encryption here.
At DropSecure, we believe that a user should never have to compromise on security or ease of use. A collaborative tool must deliver on both of these promises. Our awards, industry recognitions, and customer reviews are the testimony to the fact that DropSecure is designed with customer needs at the centre of everything.

In terms of functionality, we accept that we may not have every collaboration feature that some of the cloud service providers offer but then for us the choice was clear – security over bells and whistles. We are glad to see that many organizations have prioritized security over elaborate features. That’s precisely the reason why they are embracing DropSecure and giving us the highest ratings possible.
If you haven’t already, take our free trial today and experience the combination of security, functionality and ease of DropSecure usage today!