MFA/ Two Factor Authentication:
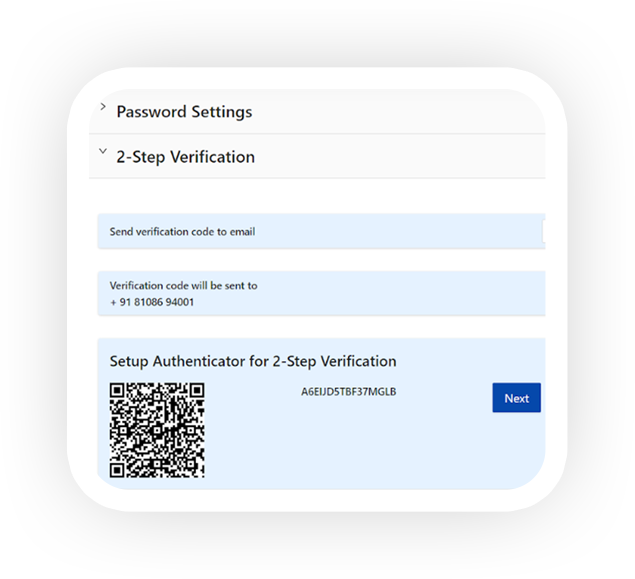
Two Factor Authentication is an added layer of security for all registered users of DropSecure. This feature is available across all user accounts which enables them to safely access sensitive data from any device or location. The authentication process can be set up with email, phone or the Authenticator App. DropSecure recommends downloading the Authenticator App and scanning the QR code provided on the Security page to complete the process and stay data secured at all times.
The 2-Step Verification feature is a must have built-in security feature in case your password is ever compromised. Once the 2-Step Verification has been set up, your sign-up process will involve authentication in two steps.- First, entering your password, which is something you know and
- Second, entering a pin from your phone/ email/ Authenticator App, which is something you have.
You can skip this step on trusted devices, by checking the box next to ‘Remember me on this device’ and selecting the number of days against this choice.
Revoke Access Controls:
Revoke simply means ‘to take back’ or ‘cancel’. This feature allows users to revoke access to files and data shared with any recipient.
Given a scenario where sensitive data was shared with person X erroneously, you as a registered user of DropSecure are able to revoke access to sensitive files with a simple slide of a button. Thereby Person X now has no access to those files. This powerful tool gives you control with simplicity.
Audit & Logging:
DropSecure provides built-in, extensive audit and logging records. It helps monitor your data and usage to increase your organizations’ cyber security measures. Audit logs are also crucial for complying with regulations such as HIPAA and PCI as well as for risk management. The Audit Logs helps Admins monitor trends of usage and reduce the chances of data leaks and other cyber security threats that can compromise your organization. These extensive logs are easily understandable and accessible making security easy for your organization.
Auditing captures the details of the unique user id, unique subject id, functions performed and the details such as date and time of the events, as well as, the information that may have changed from the performance of the event. Logging activity that is captured is the download, upload, sharing and modification of files.
Roles and Permissions:
Granular access controls are available to Super Admins, Department admins and users permitting different functionalities to be fulfilled. Granting access to particular users of particular resources helps build a blanket of security within the organization. Having this feature helps prevent data from being compromised and minimizes the chances of security breaches. DropSecure makes granting different access controls easy, simply by a click of a button. The access can be revoked or granted, making roles and permissions a way to build security with ease of use.
In secure data transfer, you would prefer to see several parameters protecting data transfer. The primary parameters include controlling who the receivers are; how long the sharing will last and what permissions the receivers have to the files.

Super Admin
- Can create new departments
- Can manage users in all departments
- Create internal or external users in any department
- Don’t necessarily have access to the data being exchanged in various departments

Department Admin
- Can manage users in their department
- Can access the all the documents in their department
- Create internal or external users in their own department
- Don’t have access to other departments
- Can’t create new departments

User
- Can only access documents they are permitted to view/download by the department admin
- View only access
- Can be given folder admin rights
Secure Drop URL:
The Secure Drop URL is a link which you can share with your clients and third parties when requesting for them to send you information. This link is unique to you and files can be transferred by any third party only to you with end-to-end encryption.
Requesting sensitive information from a third party using a secure channel ensures that the data is not deciphered by unauthorized persons. DropSecure’s Zero Knowledge Technology ensures that requesting and sharing of this information is only between the intended parties, where even we, the service provider, are unable to access the information shared.
You can share this URL with your clients so they can send you files or messages securely without registering with DropSecure.
Secure File Vault Protection:
The challenge to sharing information between senders and receivers that are not from within the same organization or corporation pose a huge risk to the security and privacy of data shared. There are many more points of exposure to data breaches leaving the organization vulnerable.
‘Secure Links’ equipped with end to end encryption and zero knowledge is the solution to protect organizations from spending millions of dollars on data recovery post a breach. The business is able to secure sensitive information from reaching unintended hands.
DropSecure generates these links when the sender (either a registered DropSecure user or unregistered user) sends data or files using the DropSecure portal. The recipient can then access this information by clicking on the ‘Secure Link’ from the email notification they receive. The receiver is verified either with login or a one time password. Decrypting this information follows DropSecure’s end-to-end encryption technology with AES-256 keys. These security features are built in with an easy to use interface.